Implement Basic Protection using AWS Managed Rules
Scenario
Your security team has prioritized protection against common attacks such as Cross-Site Scripting (XSS), path traversal, and SQL injection as a high priority. Your task is to find ways to mitigate the risks of web application attacks using AWS WAF. Your business wants a fully managed solution that does not require manually creating rules.
Instructions
Review the Web ACL configuration for the web application. Add the Core rule set and SQL database managed rule groups to it. The Core rule set includes rules that apply to most web applications, providing protection against a wide range of threats, from basic to critical. The SQL database rule group are designed to block requests related to SQL database exploitation (e.g., SQL Injection). For more information about the Core Rule Set and SQL Database Managed Rule Groups, refer to the AWS WAF documentation.
After implementing the Core rule set and the SQL Database rule group, test protections with manual and automatic scans using the WAF Dashboard.
Procedure
Add managed rules to the WAF ACL
Open the WAF ACL and navigate to the Rules tab:
Open the AWS WAF Console.
Ensure that the Global (CloudFront) region selected.
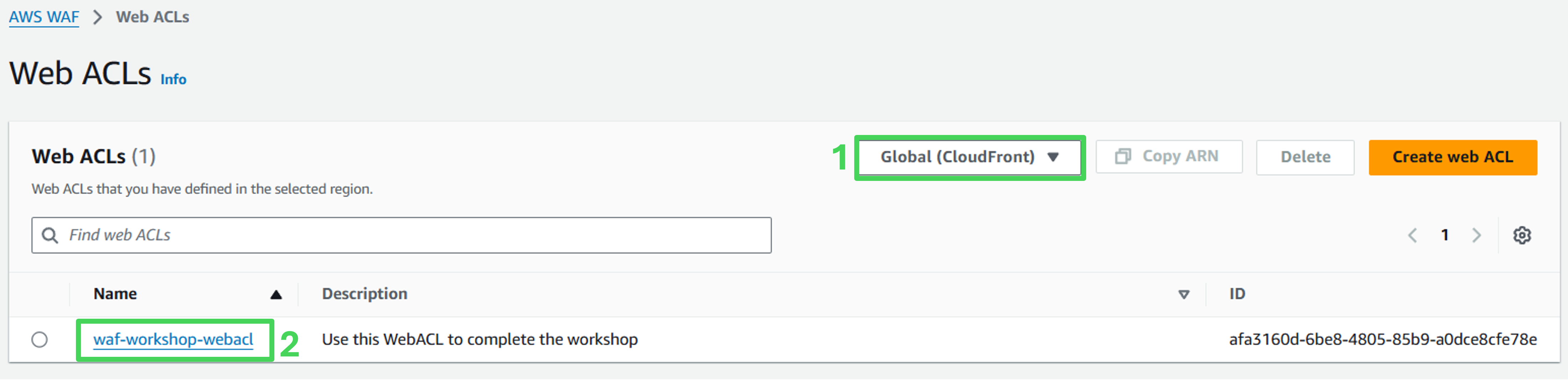 3. Open the WebACL named waf-workshop-webacl.
3. Open the WebACL named waf-workshop-webacl.
- Navigate to the Rule tab.
Add the Core rule set and the managed rule group for SQL database:
Click Add Rules, then select Add managed rule groups.
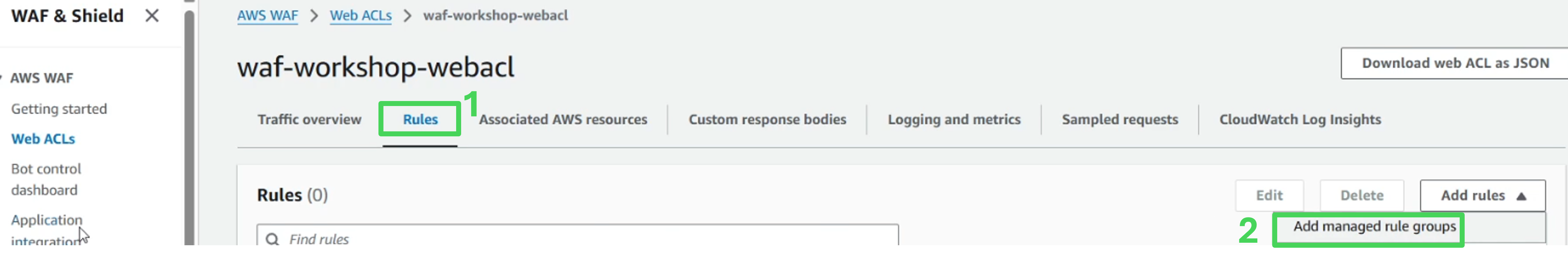
Expand the AWS managed rule groups section.
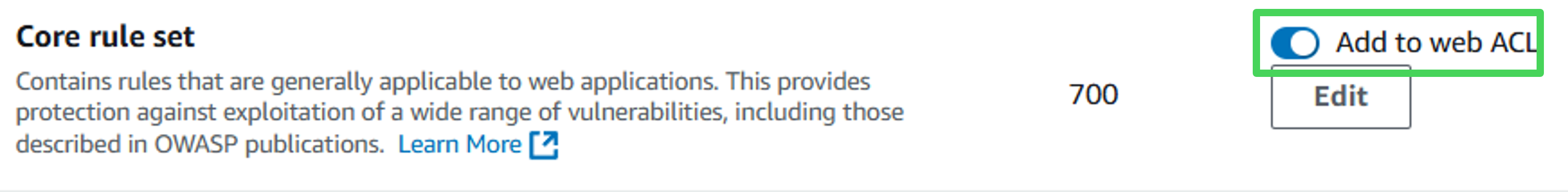
Enable the toggle for the Core rule et (turns blue). (changes color to blue)
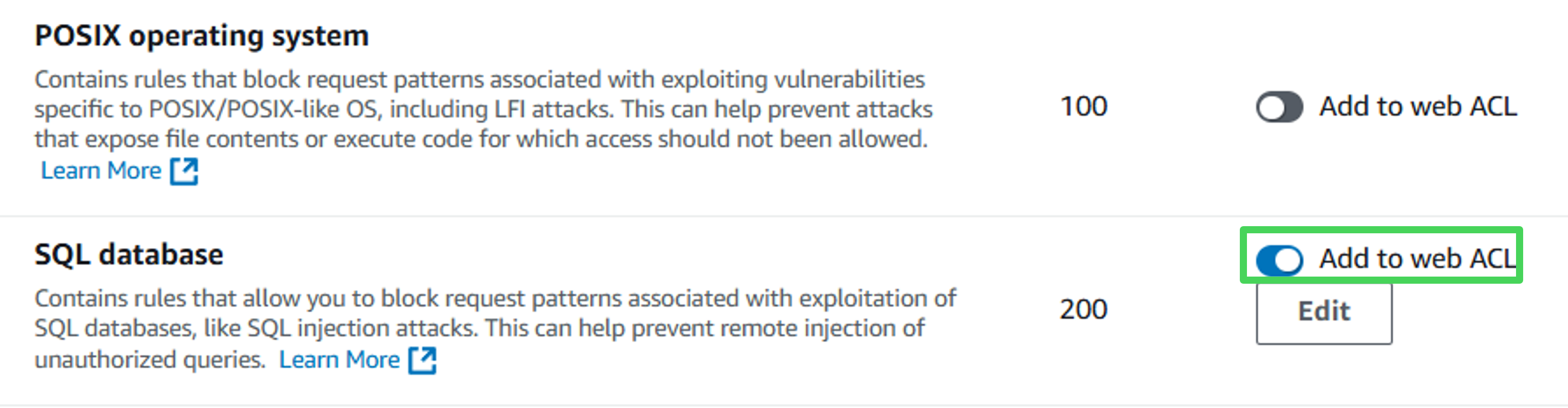
 4. Enable the toggle for the SQL database (turns blue).
4. Enable the toggle for the SQL database (turns blue).
 5. Click Add rules at the bottom of the page.
5. Click Add rules at the bottom of the page.
On the Set rule priority page, click on Save.
On the Rule tab, confirm that both the AWS Managed Common and SQLi Rule Sets have been successfully added.
You have added two managed rule sets to the WebACL. You can proceed to test the protections.
Assess the effectiveness of the protection
Perform manual protection testing following the instructions in the Evaluate section to ensure that SQL Insert, Cross-site Scripting (XSS), and Path Traversal tests are handled properly.
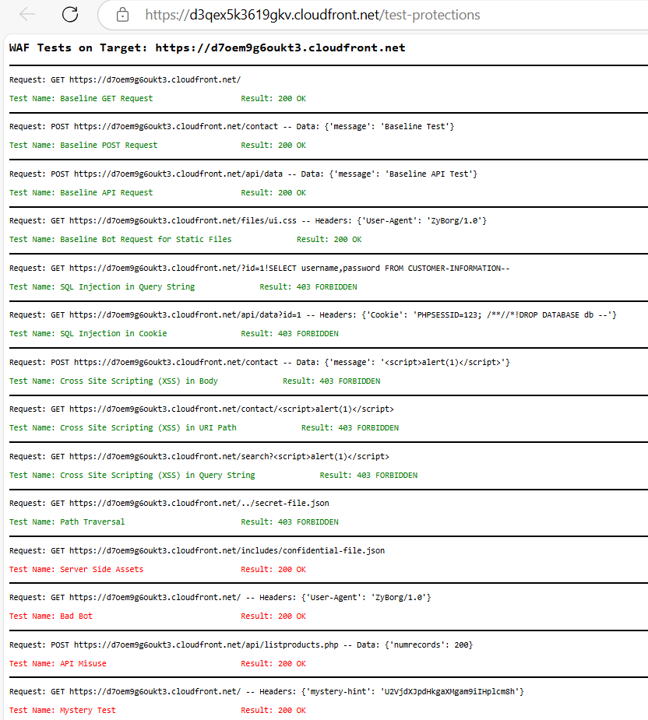 Review the progress dashboard to confirm that automatic scans for the above tests have passed.
Review the progress dashboard to confirm that automatic scans for the above tests have passed.
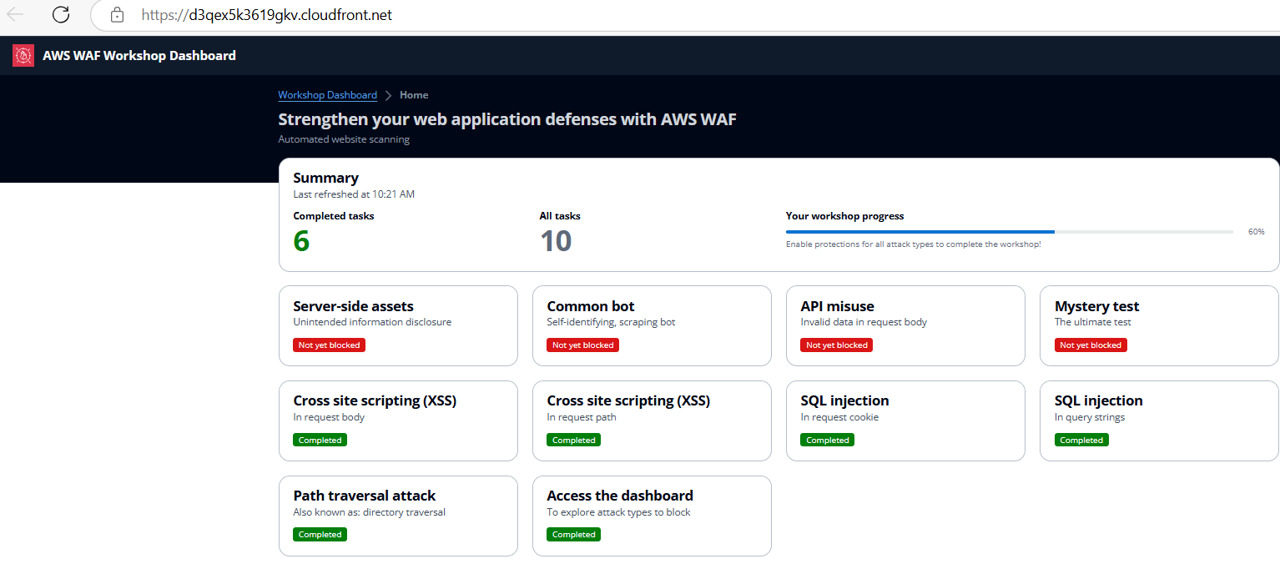 You have successfully implemented the Core rule set and the SQL database rule set, providing essential protection against web application attacks!
You have successfully implemented the Core rule set and the SQL database rule set, providing essential protection against web application attacks!