Respond to a Lambda function calling malicious IP
Scenario / Problem Statement: You have been assigned a GuardDuty finding to investigate and remediate. The GuardDuty finding type is “UnauthorizedAccess:Lambda/MaliciousIPCaller.Custom”.
Lambda Protection helps you identify potential security threats when an AWS Lambda function gets invoked in your AWS environment. When you enable Lambda Protection, GuardDuty starts monitoring Lambda network activity logs, starting with VPC Flow Logs from all Lambda functions for account, including those logs that don’t use VPC networking, and are generated when the Lambda function gets invoked. If GuardDuty identifies suspicious network traffic that is indicative of the presence of a potentially malicious piece of code in your Lambda function, GuardDuty will generate a finding.
GuardDuty monitors network activity logs generated by invoking the Lambda functions. Lambda Network Activity Monitoring includes Amazon VPC flow logs from all Lambda functions for your account, including those logs that don’t use VPC networking, and are subject to change, including expansion to other network activity such as DNS query data generated by invoking the Lambda functions. The expansion into other forms of network activity monitoring will increase the volume of data that GuardDuty will process for Lambda Protection. This will directly impact the usage cost of Lambda Protection. Whenever GuardDuty starts monitoring an additional network activity log, it will provide a notice to the accounts that have turned on Lambda Protection, at least 30 days prior to the release.
Create the Security Group
Visit the Findings page in GuardDuty. https://console.aws.amazon.com/guardduty/home?#/findings?macros=current
Add filter criteria and select Resource type and then Lambda.
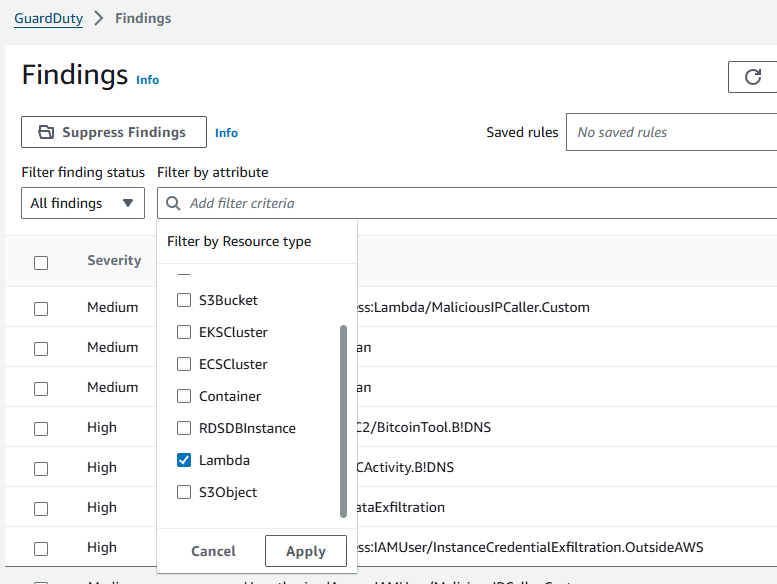
Notice there is a finding for a Lambda function that is calling a malicious IP. This finding is being generated by a Lambda that is scheduled to run every 10 minutes. The function calls an IP address that is listed on the Threat IP list active in GuardDuty named “S3BadIpAddressList”.
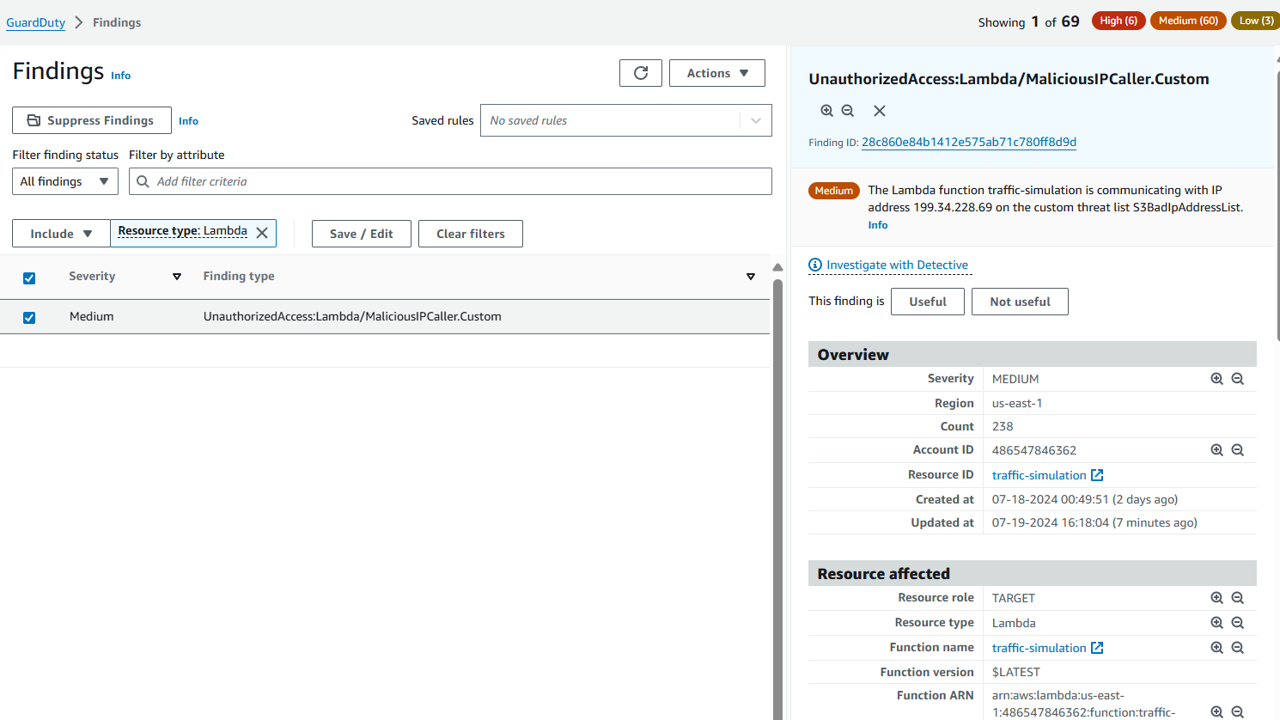
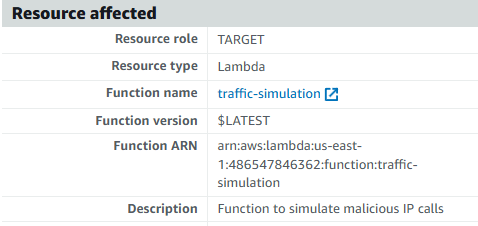
- Click on the finding to open it and review the details. Can you locate the name of the Lambda function and the IP address it is calling from the Threat IP list?
Lambda function
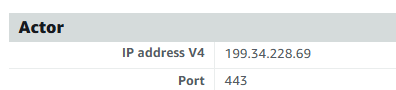
 IP:
IP:
If you want to see the configuration history of the function, you can use AWS Config. AWS Config continually assesses, audits, and evaluates the configurations and relationships of your resources on AWS, on premises, and on other clouds. Open AWS Config and navigate to the Timeline for the Lambda function, or follow this link: https://console.aws.amazon.com/config/home?#/resources/timeline?resourceId=traffic-simulation&resourceName=traffic-simulation
Click Load more at the bottom of the page until the full history is showing. Expand the oldest CloudTrail Event, then under View event, click CloudTrail. AWS CloudTrail monitors and records account activity across your AWS infrastructure, giving you control over storage, analysis, and remediation actions.
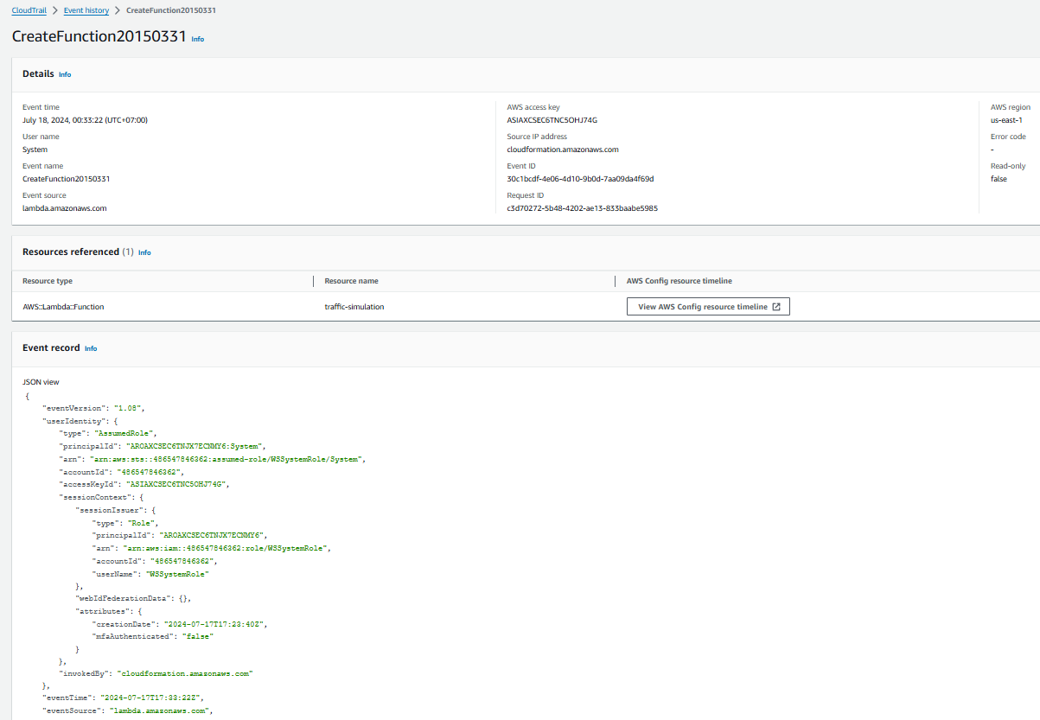
- Click the name of the event in CloudTrail. It should start with “CreateFunction…”. This will open the event record for the creation of this Lambda function. Among other things, the event record details that the function was created using CloudFormation, from a function stored in Amazon S3, by userName WSSystemRole.
 8. You may optionally delete the Lambda function from the Lambda console. Otherwise, continue to the next module.
8. You may optionally delete the Lambda function from the Lambda console. Otherwise, continue to the next module.