Setting up notifications
After Security Hub has ingested a finding identifying a threat or stating that a configuration that needs attention, the next step is take action and resolve the finding. With Amazon EventBridge, you can automate your AWS services to respond automatically to system events such as application availability issues or resource changes.
Amazon EventBridge is a serverless event bus that makes it easier to build event-driven applications at scale using events generated from AWS services. Events from AWS services are delivered to EventBridge in near-real time and on a guaranteed basis. You can write simple rules to indicate which events you are interested in and what automated actions to take when an event matches a rule. The actions that can be automatically triggered include the following:
- Invoking an AWS Lambda function
- Activating an AWS Step Functions state machine
- Notifying an Amazon SNS topic or an Amazon SQS queue
- Sending a finding to a third-party ticketing, chat, SIEM, or incident response and management tool
Security Hub automatically sends all new findings and all updates to existing findings to EventBridge as EventBridge events. You can also create custom actions that allow you to send selected findings and insight results to EventBridge. You then configure EventBridge rules to respond to each type of event.
In this module, we will create an EventBridge rule to automate notifications on a filtered list of findings from Security Hub. We will configure Amazon Simple Notification Service so we will receive email alerts when we receive a HIGH or CRITICAL severity finding in Security Hub. Amazon Simple Notification Service (Amazon SNS) is a fully managed messaging service for both application-to-application (A2A) and application-to-person (A2P) communication.
In a real-world scenario, this particular example would not scale, but it will demonstrate how AWS Security Hub works with Amazon EventBridge.
Configure Amazon Simple Notification Service topic
Navigate to Amazon SNS.
Click Topics in the left navigation.
Click Create topic.
Select Standard type.
For the name, enter “high-severity-security-hub-findings”. Result:
Leave everything else as is and click Create topic at the bottom of the page. This will create the topic.
Subscribe to the topic
From the high-severity-security-hub-findings topic page, click Create subscription.
On the Create subscription page, under Protocol, select Email.
On the Create subscription page, under Endpoint, enter your email address that you want to use for this workshop to receive notifications. You can unsubscribe at the end of the workshop.
Click Create subscription.
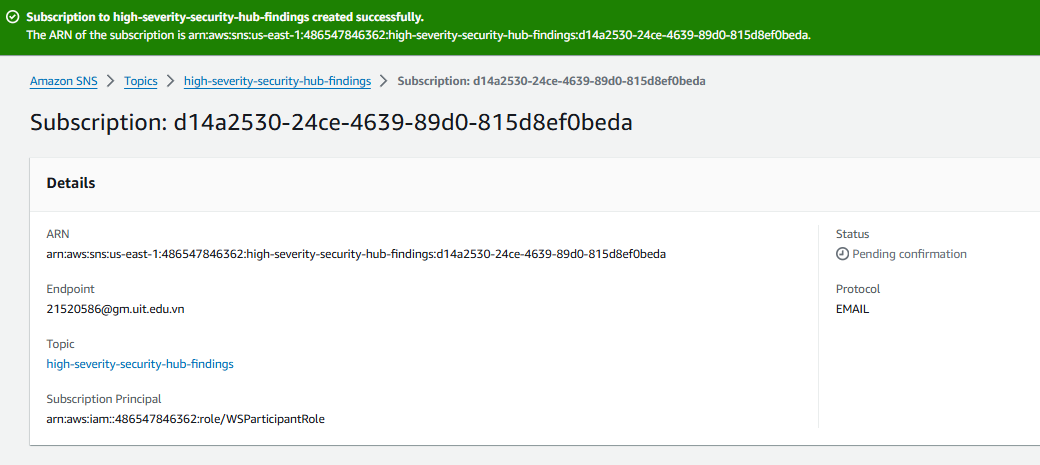
Within a couple minutes, you will receive an email at the email address you entered. Confirm the subscription by clicking Confirm subscription in the email.
Create an EventBridge Rule to send findings to the topic
Now that we have subscribed to our SNS topic, we are ready to send findings to the topic. To do this, we will create an EventBridge rule that matches Security Hub events for HIGH and CRITICAL severity findings.
Navigate to Amazon EventBridge. https://console.aws.amazon.com/events/home
Click Create rule.
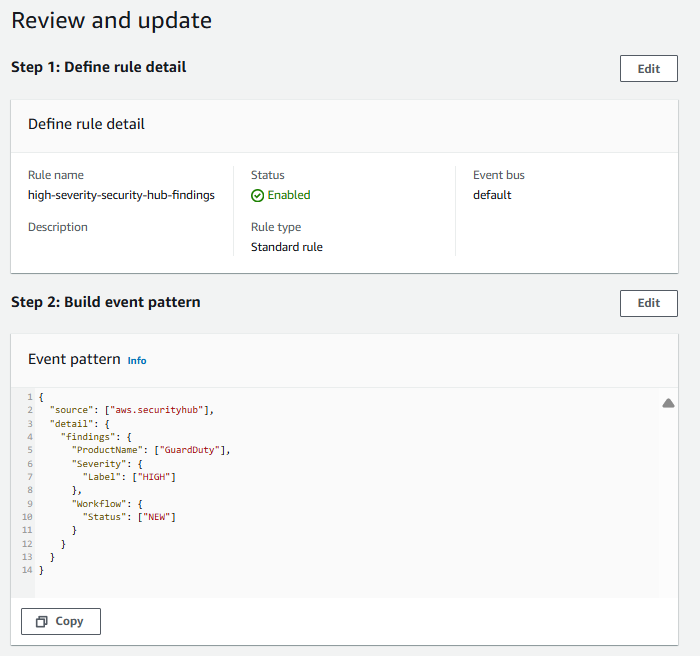
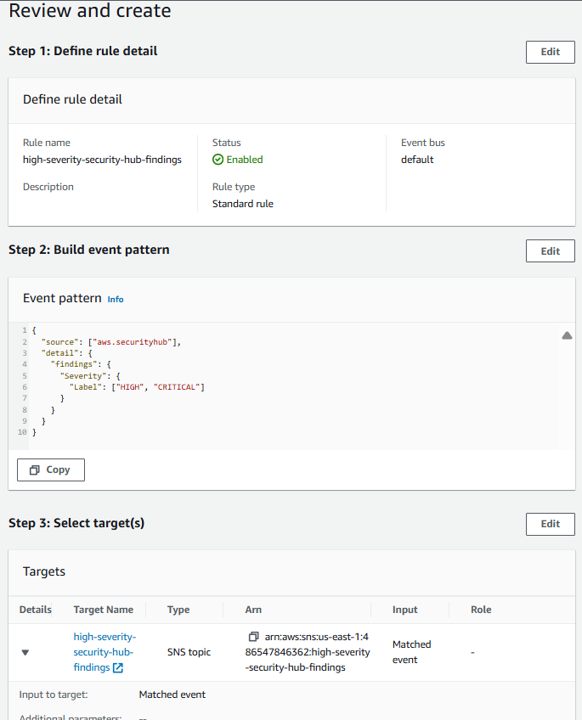
On the Define rule detail page, name your rule “high-severity-security-hub-findings”.
Click Next.
On the Build event pattern page, in the Event pattern section, click Edit pattern.
Input the following Event Pattern:
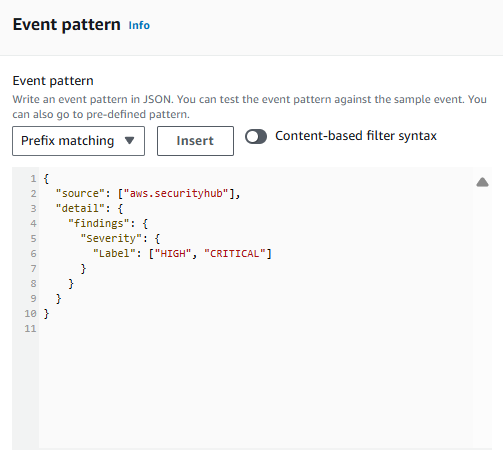
{
"source": ["aws.securityhub"],
"detail": {
"findings": {
"Severity": {
"Label": ["HIGH", "CRITICAL"]
}
}
}
}
Click Next.
On the Select target(s) page, from the Select a target dropdown, select SNS topic.
Then from the Topic dropdown, select high-severity-security-hub-findings.
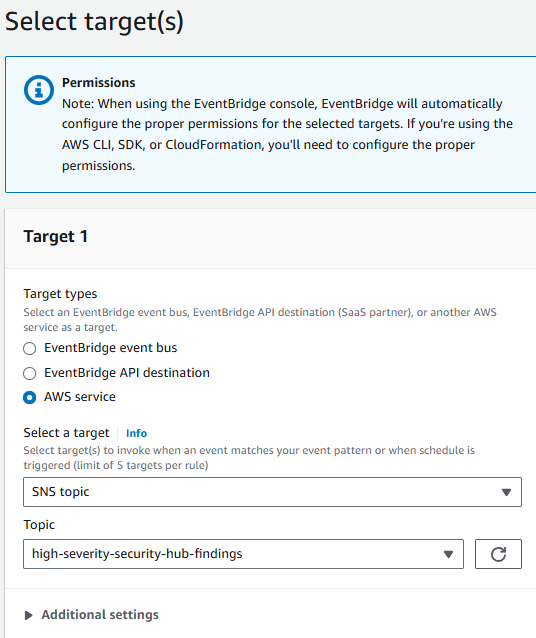
Click Next.
On the Configure tags - optional page, click Next.
On the Review and create page, click Create rule.
Test the notifications
The EventBridge rule we configured will push a notification on any update or new Security Hub finding that have a severity label of “HIGH” or “CRITICAL”. We could wait for a new or updated finding, but it will be faster to test this by updating a finding ourselves. An easy way to do this is by changing the Workflow status of a finding.
For findings, the workflow status tracks the progress of your investigation into a finding. The workflow status is specific to an individual finding. It does not affect the generation of new findings.
Return to Security Hub.
Open the Findings page.
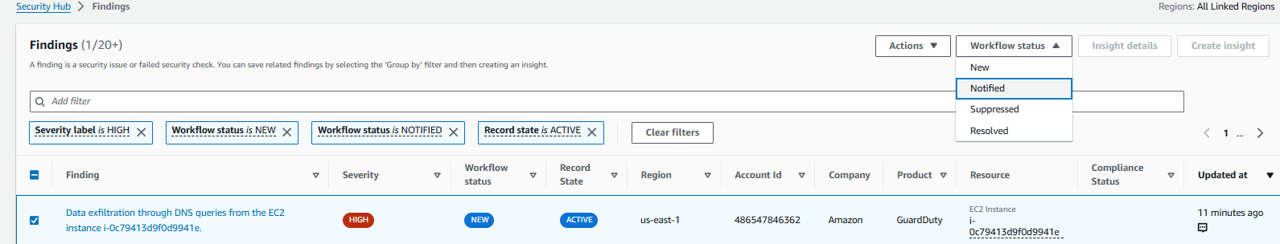
Add a new filter, for Severity label is HIGH. This is case sensitive. Click Apply.

Click the title for any of the high severity findings to open it.
Under the Workflow status dropdown in the finding details, change the workflow from New to Notified.
You will see a banner display “Successfully changed workflow status”. This update will result in you receiving an email containing the JSON for this finding. You will want to unsubscribe from these notifications before completing the workshop.
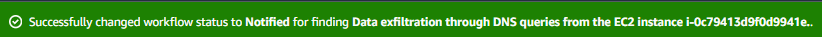
Notification:
Challenge
At this point you understand most of the basics of how AWS Security Hub works with Amazon EventBridge. Let’s put that knowledge to the test.
After configuring the notification for all HIGH and CRITICAL findings, you realized that you are getting too many notifications between resource compliance changes, the resolution of findings, and co-workers changing the workflow status of findings.
Using what you learned so far, try to modify the notification you set up to only email you findings with a HIGH severity label, that have a workflow status of New, and that Security Hub receives from GuardDuty (findings must match all 3 conditions). Amazon GuardDuty is a threat detection service that continuously monitors your AWS accounts and workloads for malicious activity and delivers detailed security findings for visibility and remediation. These are alerts you want to act on quickly.