Security Hub - Findings
Findings in Security Hub
Click on Findings from the navigation on the left in Security Hub.
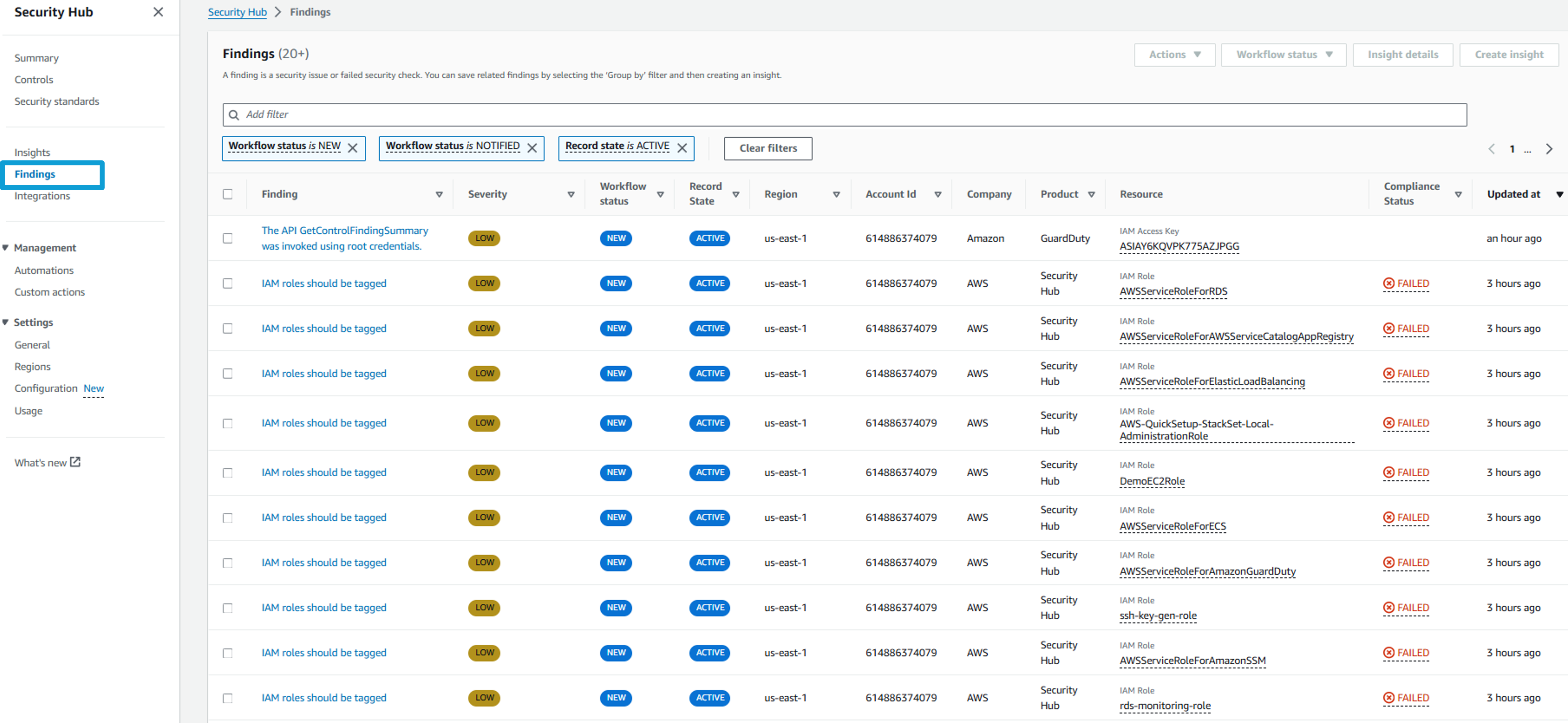
You can use filters to narrow the list of findings displayed. Click the input Add filter.
Select Product name and then input “GuardDuty” (case-sensitive). Click Apply.
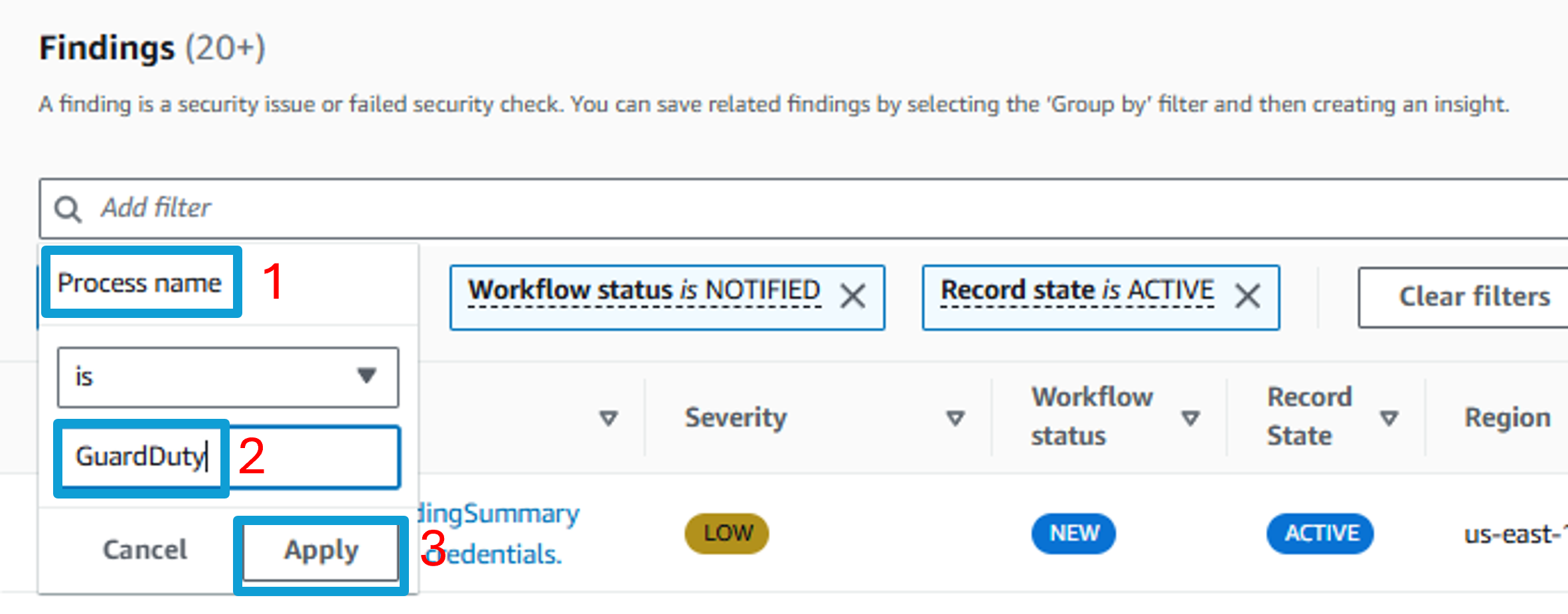
This will display all the findings that Security Hub has received from the threat detection service, GuardDuty. There are many Security Hub findings listed here.
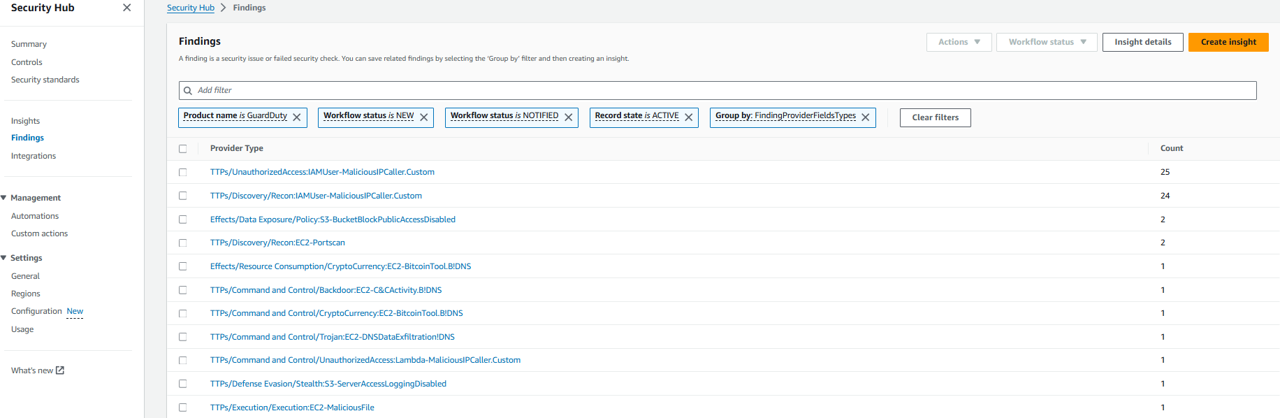 Try adding a filter to narrow the list down to high severity findings. Click the Add filters again.
Try adding a filter to narrow the list down to high severity findings. Click the Add filters again.From the dropdown, select Severity label and choose is and then input HIGH. This is case-sensitive. Click Apply.
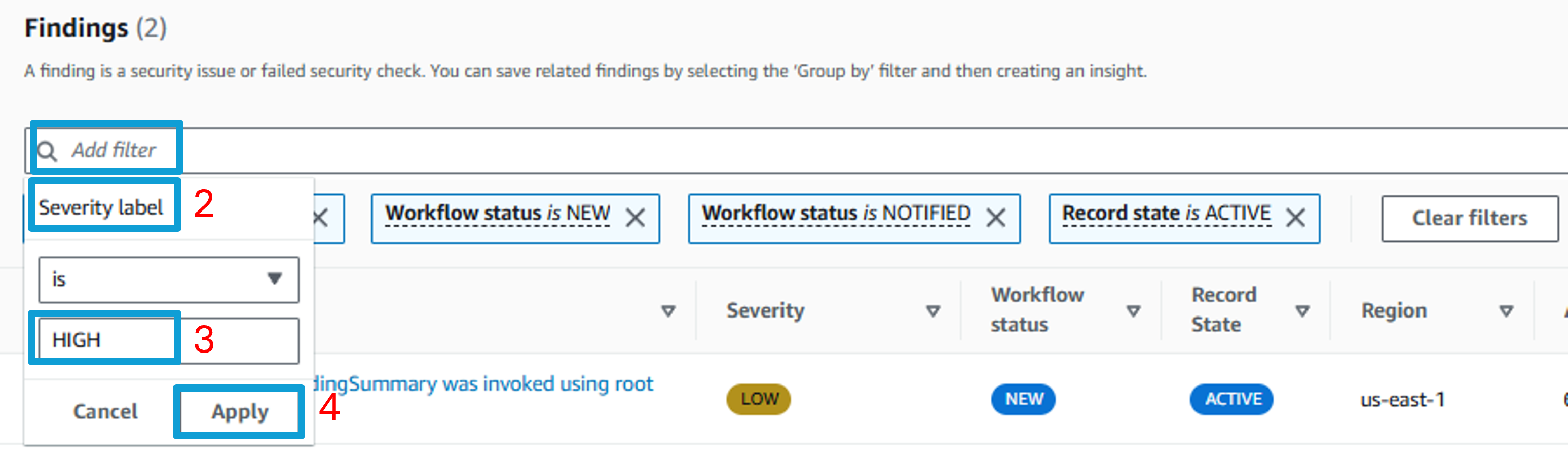 Result:
Result:
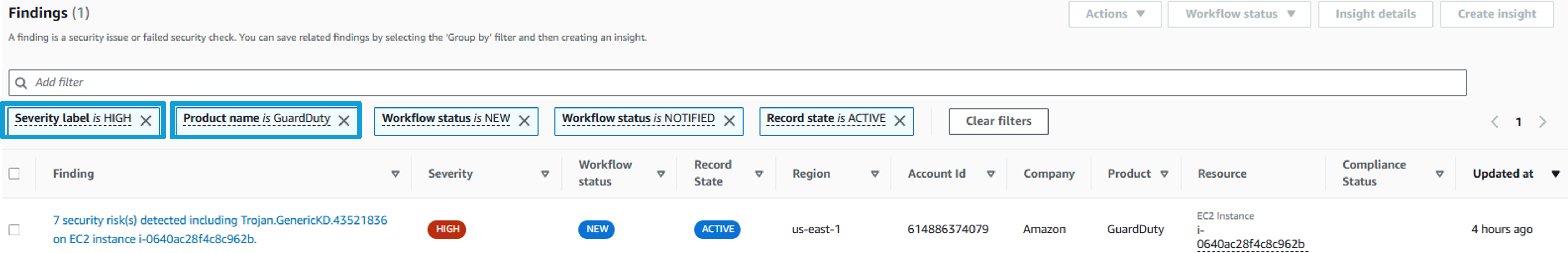
Pick one of the findings and click on the title. This opens the finding details pane. Expand all the sections and take a few minutes to review the information here. You can see the description, a link to remediation instructions, information about the resource, and more.
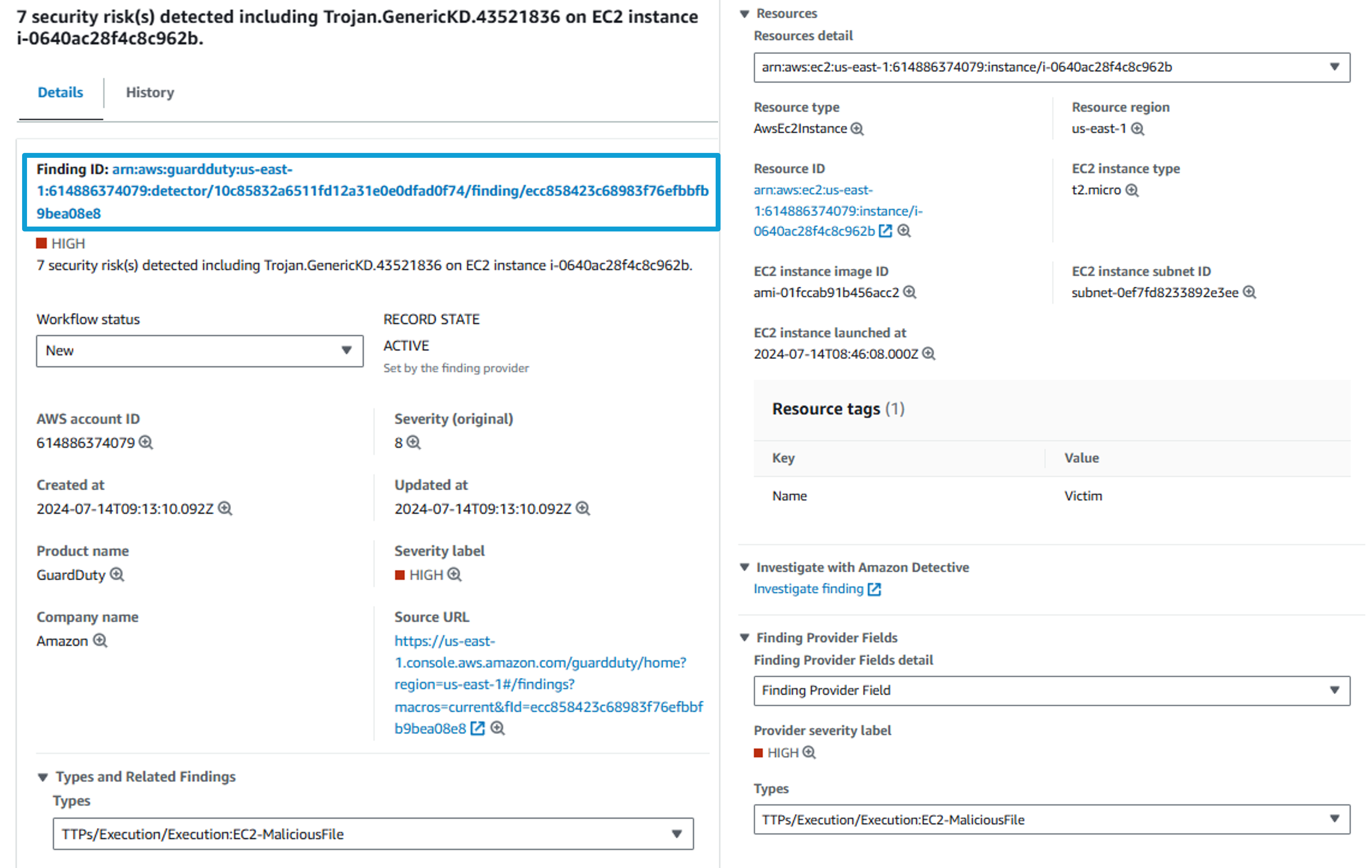
In the finding details pane click the finding ID link at the top of the pane to display the complete JSON for the finding. The finding JSON can be downloaded to a file if ever needed for further investigation.
Close out of the JSON pop-up by clicking the X in the top right.
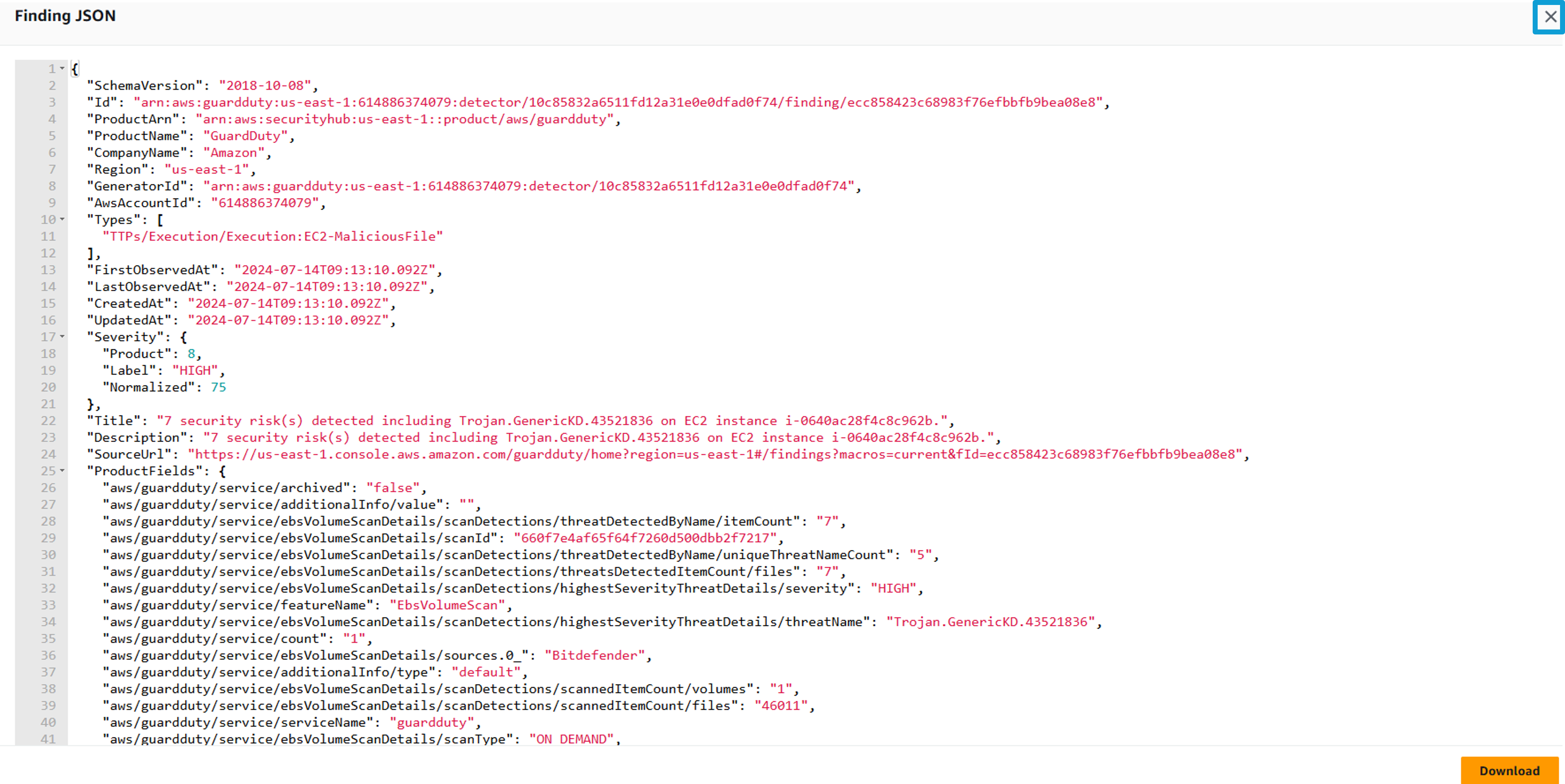
At the top of the finding details, open the History tab to view a chronological list of all changes that have been made to the finding. The transparency of finding history helps you identify potential security risks more quickly and take proactive steps to mitigate them.
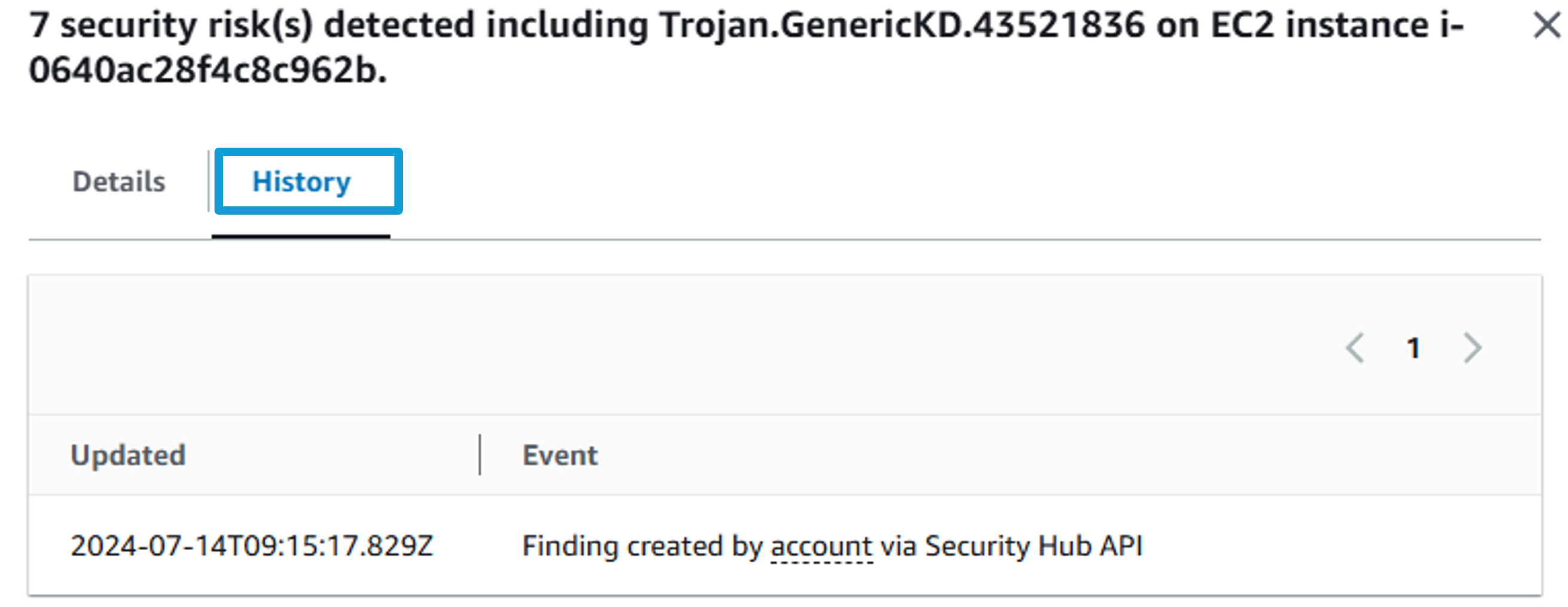
Close the finding details pane by clicking the X in the top right, but stay on the Findings page.
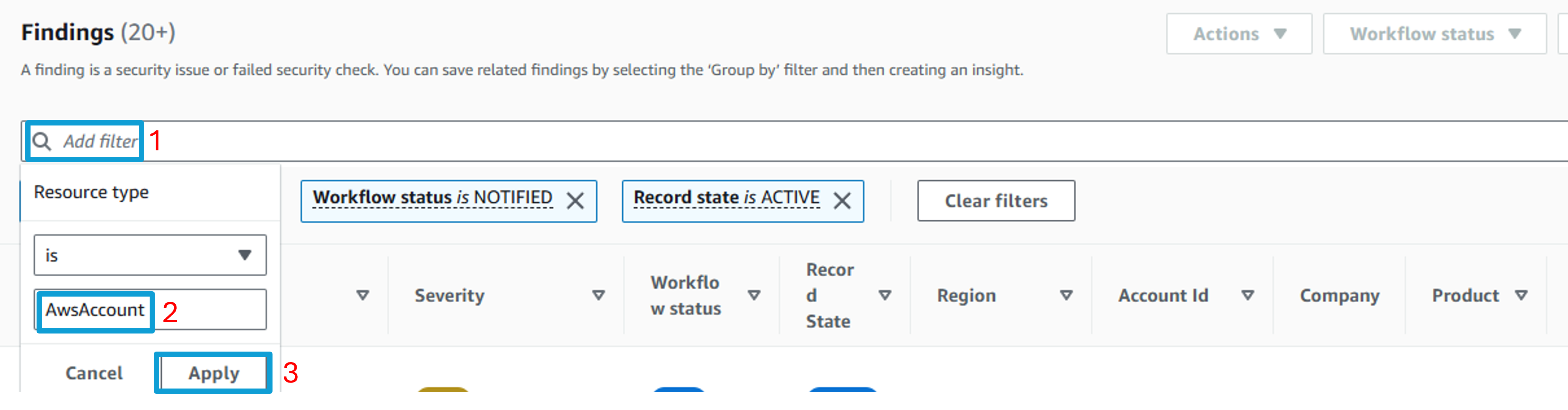
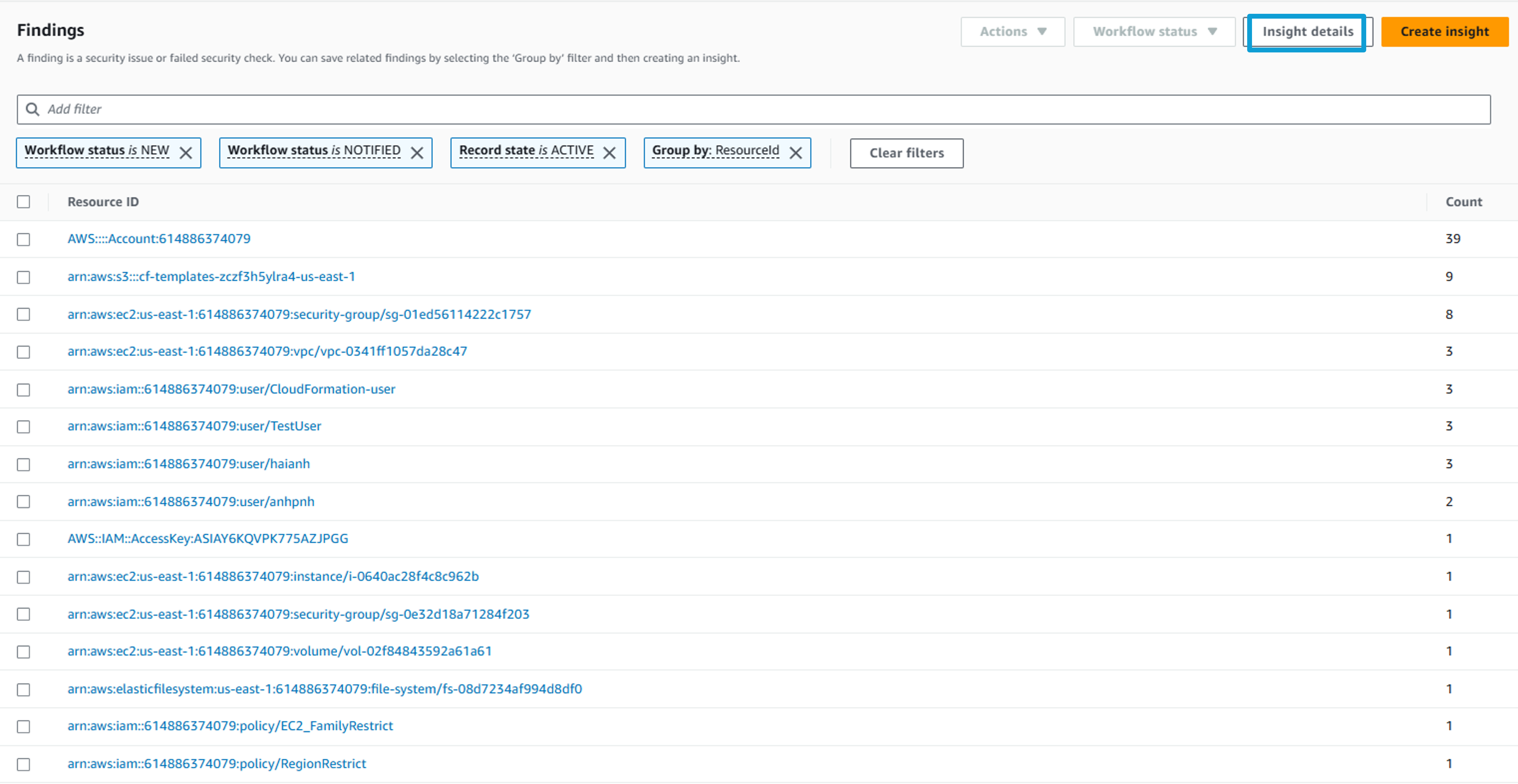
Try to understand what resources in our environment are generating the most findings. Remove all the filters. Then add a new filter, select Resource type and choose is not and then input AwsAccount. Click Apply.
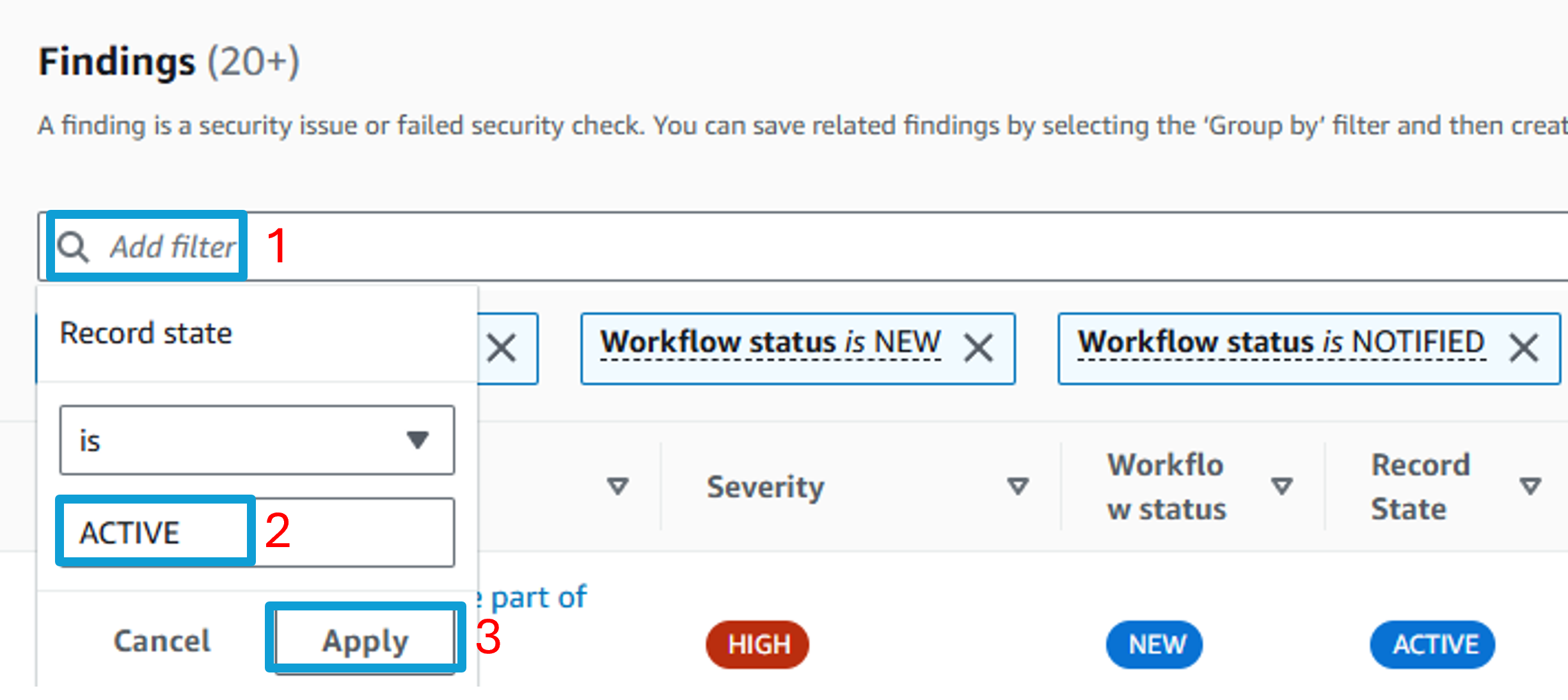
Add another filter. Select Record state, choose is, and then input ACTIVE. Click Apply.
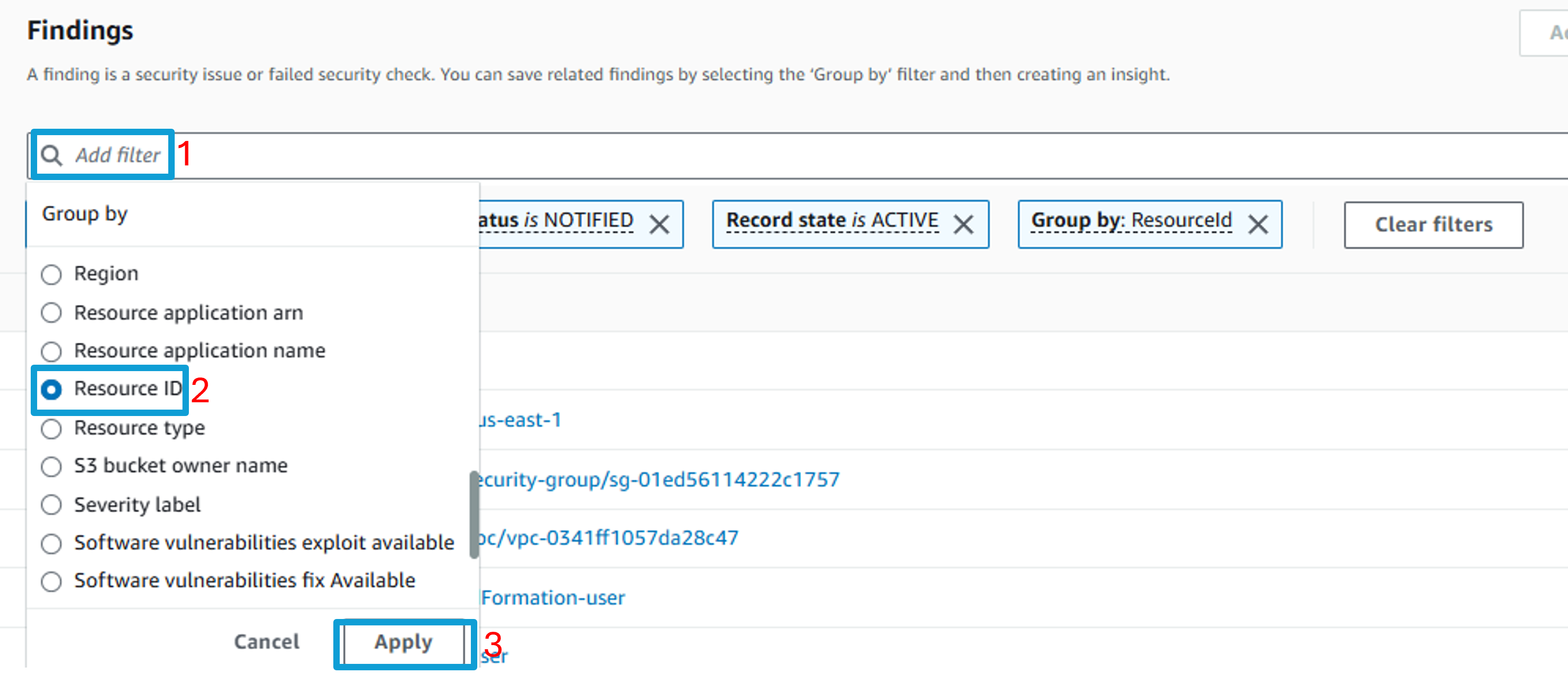
Click Add filters in the search bar again. This time, select Group by and choose ResourceId. Click Apply. This list shows you the number of findings per resource.
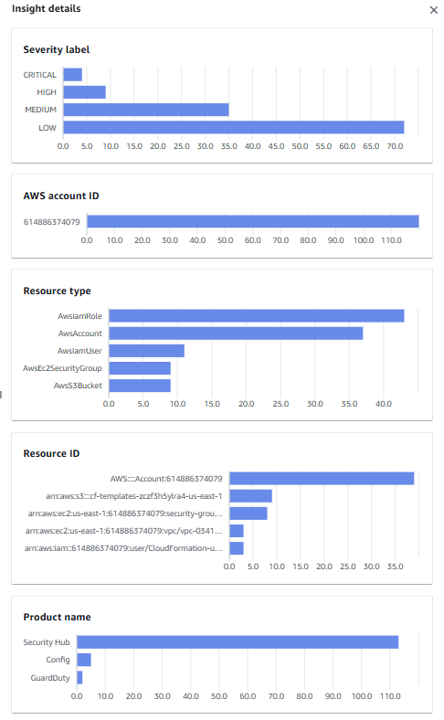
View detail by clicking Insight details:
Watch other findings filtered by TTPs/Discovery/Recon:IAMUser-MaliciousIPCallerCustom provider type, produced by GuardDuty
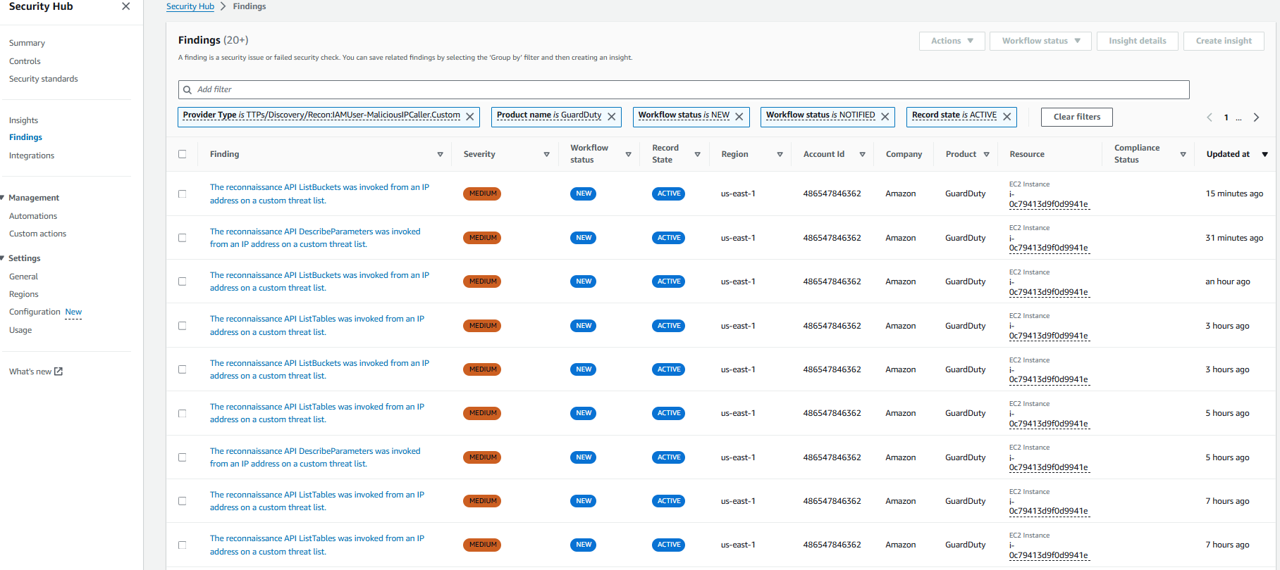
Click one finding to view more detailed.
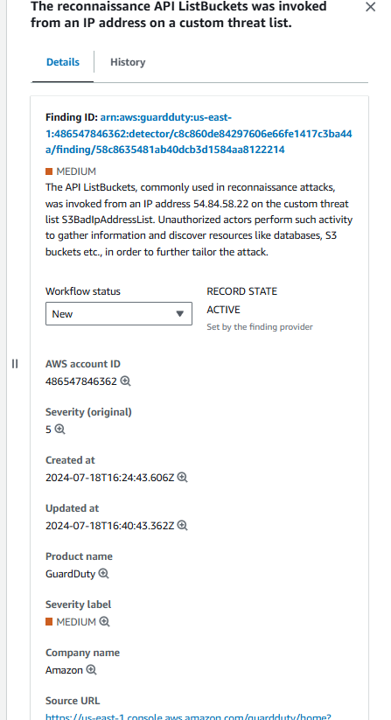 It says that an API ListBuckets was invoked by Unauthorized actors, recognized from the IP on the custom threat list bucket.
It says that an API ListBuckets was invoked by Unauthorized actors, recognized from the IP on the custom threat list bucket.Watch more findings produced by Inspector
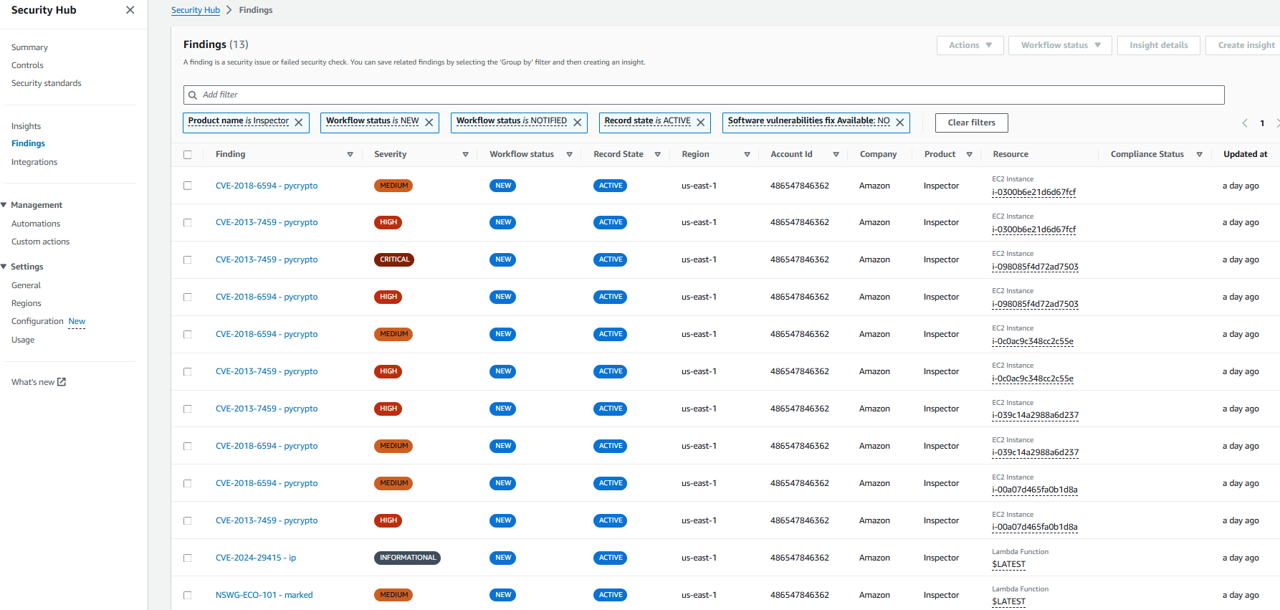 Those findings are created when Inspector detects vulnerabilities by scanning EC2 instances.
Those findings are created when Inspector detects vulnerabilities by scanning EC2 instances.